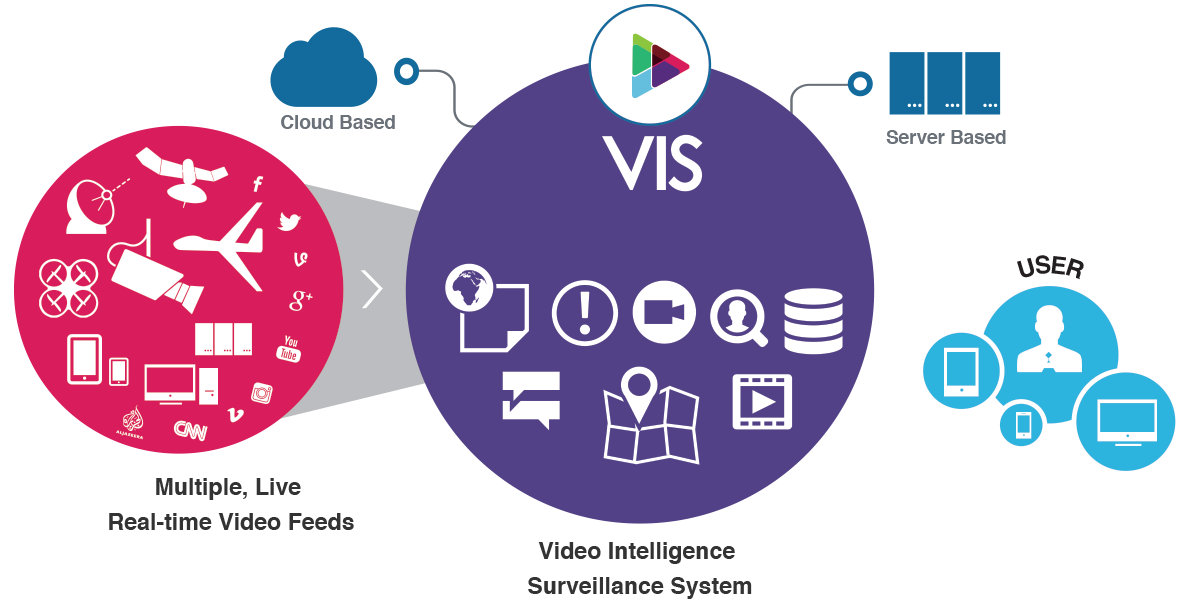
VIS is a video and data management platform that includes ingestion, storage, search, workflow, analysis, and reporting. VIS delivers a simple and intuitive experience that allows all cameras and sensors to deliver fused, actionable data in real time to whoever needs it in a secure and auditable environment.
VIS accepts information streams from all digital sources, including commercial unmanned aircraft (drones), CCTV, lapel and dashboard cameras, the web, and mobile IOS and Android devices, sensors (unattended ground sensors, chemical, radiological, biological, etc.).
VIS provides tagging and data management, long-term data protection and secure storage, extensive search capabilities, data privacy, and fully certified chain of custody and audit capabilities.VIS platform can be deployed in a cloud (your cloud or ours, public or private) or in an existing data center on hardware you already own or it can be delivered as a stand-alone appliance.
- Mission or Event Wall
- Geospatial Integration
- Video Player
- Chats
- Alerts
- Map Integration
- Video
- Video Management
- File Management
- Search
- Geospatial Data Management
- Airborne Cameras
- Mobile Devices
- Fixed Cameras
- Mobile Cameras
- Sensors
- News Feeds
- Databases and Reports
- Social Media
Why VIS System?
VIS is extensible. It is designed to connect to any 3rd party analytics program (license plate readers, facial recognition, change detection, object recognition, etc.) via its open API.
A sophisticated rules engine, reporting tools, integrated mapping, and a tried and tested interface (including secure chat and alerts) brings a clean and familiar user experience with a minimal training.
Out of the box, VIS is configured and ready to use. VIS is available as an Enterprise solution that sits behind the customer’s own firewall or in their private cloud.
In a cost effective manner, VIS delivers:
- Ingestion of virtually any video source and delivery (live or archive) to virtually any network-connected device
such as iOS, Android, PC/Mac - Access – Cloud-based or Server-based content anywhere, anytime, any device
- Plan – Identify, tag and prioritize what needs to be observed
- Search – Compare live events to past coverage
- Report – Tell the story
- Share and Collaborate – Annotate, distribute, message
- Privacy and Security – Maintain chain-of-custody, encrypted delivery, audit trail
- API
Current Trends And Gaps
The Trend
- Increased use of video surveillance
- Migration from analog to digital and IP-based cameras
- Migration from labor-intensive video surveillance to computer automated video surveillance
- Technology maturity
- Cost reduction in hardware
- Human operators entail high cost & high rate of overlooked events
- Volume of video and imagery is skyrocketing
It is not only about video… It is about deriving timely/preventive
actionable intelligence from the video that can be accessed
from anywhere in a secure way.
The Gap
- No simple video data collection and analytic tools are available to non-government entities
- Existing technical approach is prohibitively expensive and not mass market scalable
- There is no product that merges the surveillance and analytics power of Unmanned Systems and fixed
surveillance systems in a secure way - Different platforms – proprietary formats, evolving requirements – not just video itself, but video stream metadata
- Telemetry data – remains frequently proprietary and unique to the vendor
- Big Data Problem – having too much data is the same as having no data
- Security Considerations – Data Privacy / Data Protection / Chain-of-Custody / Auditing of Access and Use
- Cyber Security Considerations – Encryption of Data-at-Rest / Encryption of Data-in-Transmission / Auditing of System

